By directing the information visitors to move within an encrypted channel, SSH seven Days tunneling adds a essential layer of security to purposes that do not support encryption natively.
These days lots of buyers have by now ssh keys registered with services like launchpad or github. These might be conveniently imported with:
Yeah, my point was not that shut supply is better but only that open up supply tasks are uncovered because there are several projects which can be commonly utilized, take contributions from any one on the net, but have only a handful of maintainers.
Our servers are on the net 24 several hours and our servers have endless bandwidth, earning you snug making use of them everyday.
We safeguard your Internet connection by encrypting the data you mail and get, enabling you to surf the internet safely and securely despite where you are—at your house, at perform, or any place else.
which describes its Key operate of creating secure interaction tunnels in between endpoints. Stunnel employs
The applying uses the SSH link to connect to the appliance server. When tunneling is enabled, the appliance connects to a local host port that the SSH consumer listens on. The SSH consumer then sends the application towards the server through an encrypted tunnel.
“Unfortunately the latter looks like the more unlikely clarification, given they communicated on different lists with regards to the ‘fixes’” delivered in the latest updates. These updates and fixes are available listed here, right SSH Websocket here, right here, and here.
An SSH authentication backdoor is surely worse than the Debian weak keys incident as well as even worse than Heartbleed, the two most infamous Linux safety incidents that I can visualize. In all probability this would are actually abused to hack most if not the entire Fortune 500, apart from Mr. Freund decided to investigate some smaller efficiency difficulty that anyone else might have dismissed as unimportant. We are spared only because of sheer dumb luck. This person has probably just averted no less than billions of bucks value of damages. Are not able to emphasize enough how grateful we need to be to him at this time.
The backdoor is created to allow a destructive actor to break the authentication and, from there, get unauthorized entry SSH 30 days to the whole process. The backdoor operates by injecting code during a vital phase of your login method.
There are numerous applications offered that enable you to conduct this transfer and several operating techniques like Mac OS X SSH WS and Linux have this capability in-built.
An inherent function of ssh is that the conversation concerning the two computer systems is encrypted that means that it's well suited for use on insecure networks.
Pc. As an example, when you created an area tunnel to obtain an online server on port eighty, you could potentially open up an internet
To help make your OpenSSH server Display screen the contents of the /etc/issue.Internet file as being a pre-login banner, just incorporate or modify this line while in the /and so forth/ssh/sshd_config file:
 Tia Carrere Then & Now!
Tia Carrere Then & Now!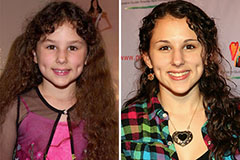 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Jason J. Richter Then & Now!
Jason J. Richter Then & Now! David Faustino Then & Now!
David Faustino Then & Now! Catherine Bach Then & Now!
Catherine Bach Then & Now!